3D printing with Prusa i3 MK3S
3D printing is additive technology for device prototyping. If you are interested in budget but very durable and affordable device i can recommand you printers by Joseph Prusa (homepage https://www.prusa3d.com/ ).
World known model is Prusa i3 MK3S taht can be obtainted as fully assemled model https://shop.prusa3d.com/en/3d-printers/181-original-prusa-i3-mk3s-3d-printer.html for 999€ or as kit with lower cost 769€ https://shop.prusa3d.com/en/3d-printers/180-original-prusa-i3-mk3s-kit.html .
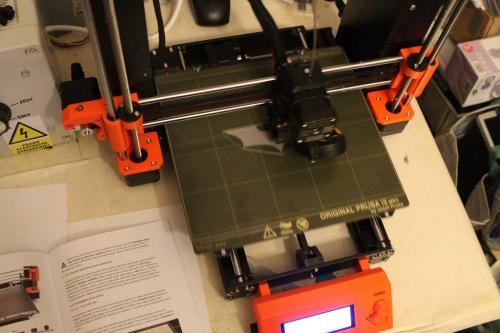
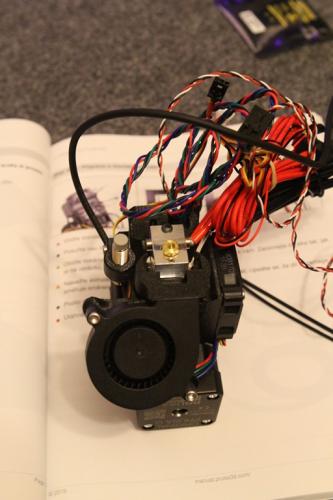
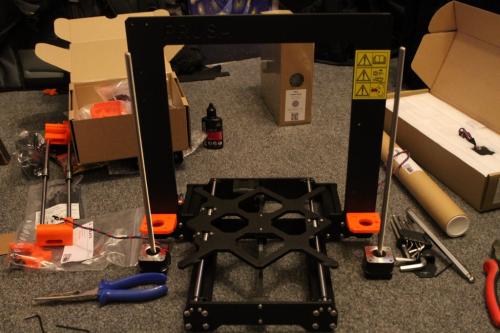
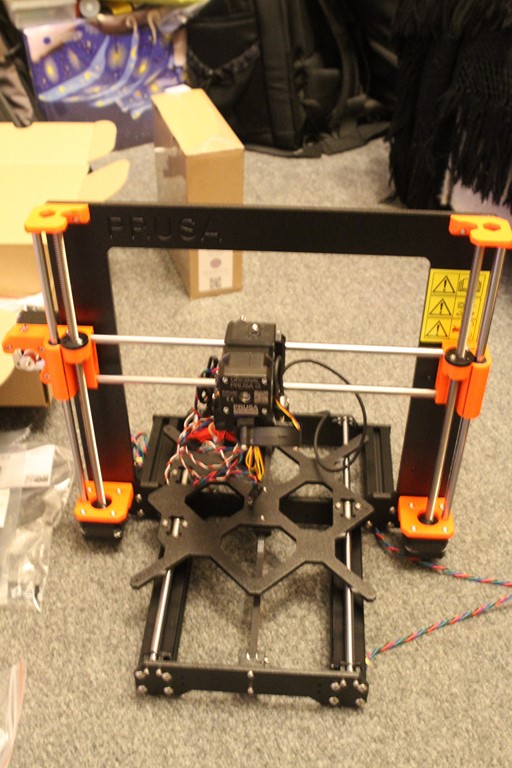
If you have a time the best way for obtaining a prusa 3D printer is by assembling it. Next galleery show how i build my printer.
#bwg_container1_0 { display: table; /*visibility: hidden;*/ } #bwg_container1_0 * { -moz-user-select: none; -khtml-user-select: none; -webkit-user-select: none; -ms-user-select: none; user-select: none; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_image_wrap_0 { background-color: #000000; width: 800px; height: 600px; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_image_0 { max-width: 800px; max-height: 510px; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_embed_0 { width: 800px; height: 510px; } #bwg_container1_0 #bwg_container2_0 #bwg_slideshow_play_pause_0 { background: transparent url("https://www.cdesigner.eu/wp-content/plugins/photo-gallery/images/blank.gif") repeat scroll 0 0; } #bwg_container1_0 #bwg_container2_0 #bwg_slideshow_play_pause-ico_0 { color: #FFFFFF; font-size: 60px; } #bwg_container1_0 #bwg_container2_0 #bwg_slideshow_play_pause-ico_0:hover { color: #DBDBDB; } #bwg_container1_0 #bwg_container2_0 #spider_slideshow_left_0, #bwg_container1_0 #bwg_container2_0 #spider_slideshow_right_0 { background: transparent url("https://www.cdesigner.eu/wp-content/plugins/photo-gallery/images/blank.gif") repeat scroll 0 0; } #bwg_container1_0 #bwg_container2_0 #spider_slideshow_left-ico_0, #bwg_container1_0 #bwg_container2_0 #spider_slideshow_right-ico_0 { background-color: #000000; border-radius: 20px; border: 0px none #FFFFFF; box-shadow: ; color: #FFFFFF; height: 40px; font-size: 20px; width: 40px; opacity: 1.00; } #bwg_container1_0 #bwg_container2_0 #spider_slideshow_left-ico_0:hover, #bwg_container1_0 #bwg_container2_0 #spider_slideshow_right-ico_0:hover { color: #DBDBDB; } #spider_slideshow_left-ico_0{ left: -9999px; } #spider_slideshow_right-ico_0{ left: -9999px; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_image_container_0 { bottom: 90px; width: 800px; height: 600px; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_filmstrip_container_0 { display: table; height: 90px; width: 800px; bottom: 0; } /* Filmstrip dimension */ #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_filmstrip_0 { left: 20px; width: 760px; /*z-index: 10106;*/ } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_filmstrip_thumbnails_0 { left: 0px; width: 2771px; height: 90px; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_filmstrip_thumbnail_0 { width: 161px; height: 90px; margin: 0 1px; border: 1px none #000000; border-radius: 0; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_thumb_active_0 { border: 0px solid #FFFFFF; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_thumb_deactive_0 { opacity: 0.80; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_filmstrip_left_0, #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_filmstrip_left_disabled_0 { background-color: #303030; display: table-cell; width: 20px; left: 0; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_filmstrip_right_0, #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_filmstrip_right_disabled_0 { background-color: #303030; display: table-cell; right: 0; width: 20px; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_filmstrip_left_0 i, #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_filmstrip_right_0 i, #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_filmstrip_left_disabled_0 i, #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_filmstrip_right_disabled_0 i { color: #FFFFFF; font-size: 20px; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_filmstrip_left_0 { display: none; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_filmstrip_left_disabled_0, #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_filmstrip_right_disabled_0 { display: none; opacity: 0.3; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_filmstrip_left_disabled_0 { display: table-cell; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_watermark_spun_0 { text-align: right; vertical-align: bottom; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_title_spun_0 { text-align: right; vertical-align: top; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_description_spun_0 { text-align: left; vertical-align: bottom; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_watermark_image_0 { max-height: 90px; max-width: 90px; opacity: 0.30; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_watermark_text_0, #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_watermark_text_0:hover { text-decoration: none; margin: 4px; position: relative; z-index: 15; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_title_text_0 { font-size: 16px; color: #FFFFFF !important; opacity: 0.70; border-radius: 5px; background-color: #000000; padding: 5px 10px 5px 10px; margin: 5px; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_description_text_0 { font-size: 14px; color: #FFFFFF !important; opacity: 0.70; border-radius: 0; background-color: #000000; padding: 5px 10px 5px 10px; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_description_text_0 * { text-decoration: none; color: #FFFFFF !important; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_dots_0 { width: 10px; height: 10px; border-radius: 10px; background: #292929; margin: 1px; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_dots_container_0 { width: 800px; bottom: 0; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_dots_thumbnails_0 { height: 12px; width: 204px; } #bwg_container1_0 #bwg_container2_0 .bwg_slideshow_dots_active_0 { background: #292929; border: 2px solid #FFC933; }
Assembling kit include great assembling manual, but you can in all time refer online manual here https://help.prusa3d.com/en/category/original-prusa-i3-mk3-kit-assembly_336. Another way how to preare for buld is through youtube bulding marathons. As examle of these bulding marathons you can watch:
or as very quick preview
After successfull assembling you must gou through selftest of device. All axis callibration process and very crucial part of all good print is Z-axis calibration and when is necessary live Z- adjustment. All my mistakes are related to:
- bad Z- axis calibration – to low or to high position of extruder nozzle
- loosen gear feeding filament in extruder (inconsistent print)
- innapropriate material for printedobjects (bad results if you use ABS for higher model and room temperature is not constant)
Quick introduction of most common problems and ho to suppress it are contained in next video