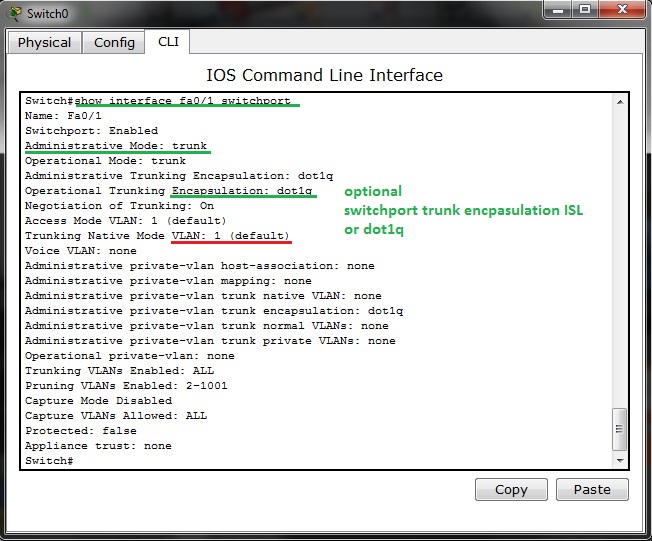
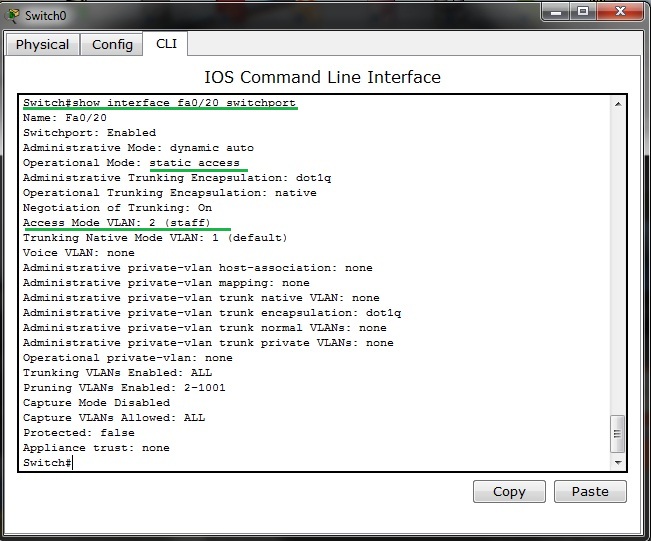
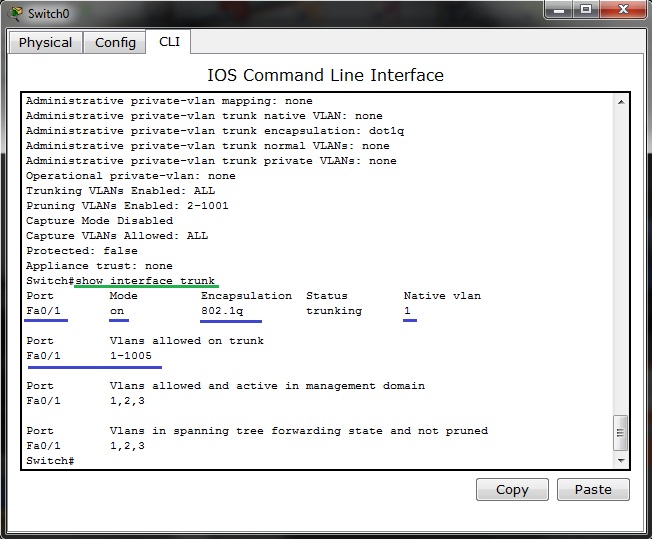
17. Port security on access layer switchport
Port security is feature that enable permit or deny traffic for end user PCs connected to access layer switch. Port security enable specify a group of valid MAC address on port. If maximum secure MAC address is reached then security violation modes lead to protect, restrict or shutdown of port.
There are 3 ways how to configure port security:
1) Static secure MAC addresses – manually configured with
switchport port-security mac-address MAC_ADDRESS
2) Dynamic secure MAC address – dynamic learned and stored only in address table (after restart cleared)
3) Sticky secure MAC address – mac address are learned dynamically and saved in running config (next can be merged with startup config).
Default port security:
– disabled on port -> switchport port-security
– maximum nr. of secure MAC: 1
– violation mode: shutdown
– sticky address learning: disabled
Sample configs:
A) Dynamic port security configuration
s1#configure terminal
s1(C)# interface FastEthernet0 0/10
s1(c-if)#switchport mode access
s1(c-if)#switchport port-security
s1(c-if)#end
B) Sticky port security – can configure max. nr. of secure mac address, in this example we configure shutdown as the violation mode
s1#configure terminal
s1(C)# interface FastEthernet0 0/10
s1(c-if)#switchport mode access
s1(c-if)#switchport port-security (enable port security)
s1(c-if)#switchport port-security maximum 20 (maximum nr. of secure address)
s1(c-if)#switchport port-security mac-address sticky (enable sticky learning)
s1(c-if)#end
Table: Security violation modes
|
Violation mode |
Forward traffic |
Send syslog message |
Display error message |
Increase violation counter |
Shuts down port |
|---|---|---|---|---|---|
| protect | no | no | no | no | no |
| restrict | no | yes | no | yes | no |
| shutdown | no | yes | no | yes | yes |
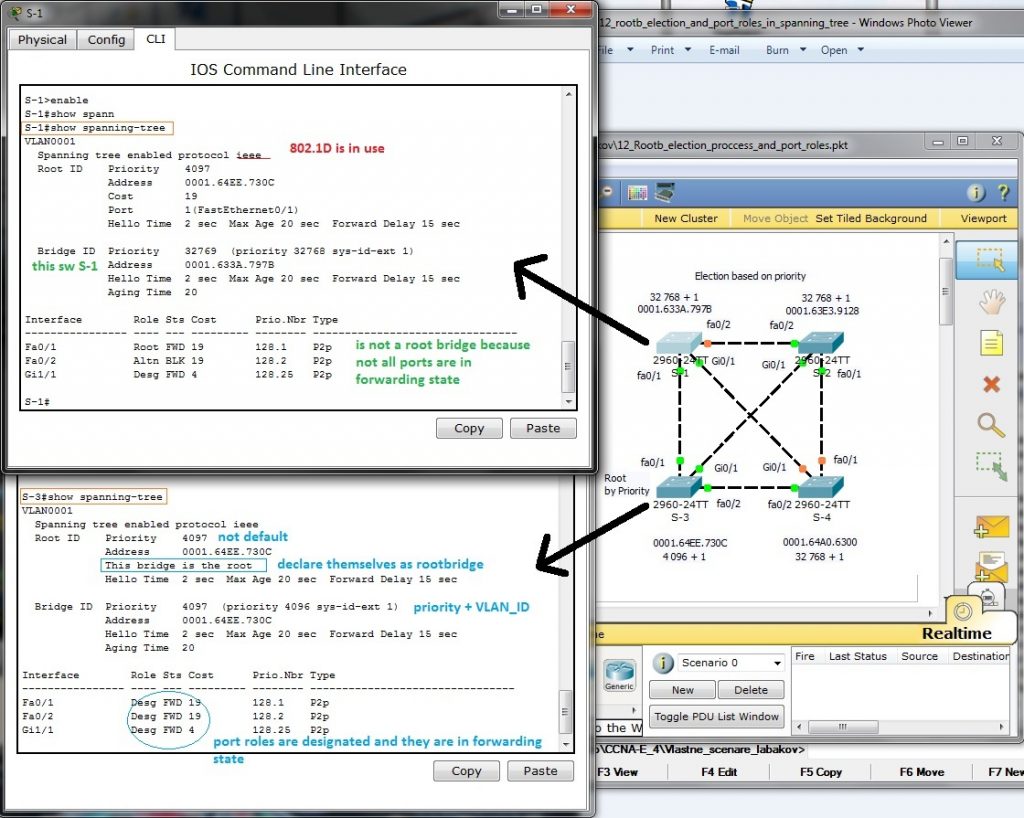
Verification commands:
- show port-security [interface interface-id]
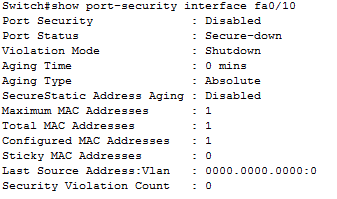
- show port-security [interface interface-id] address
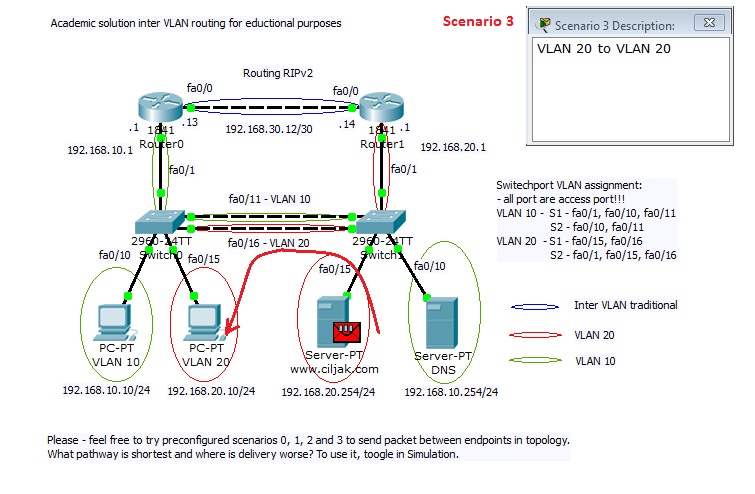
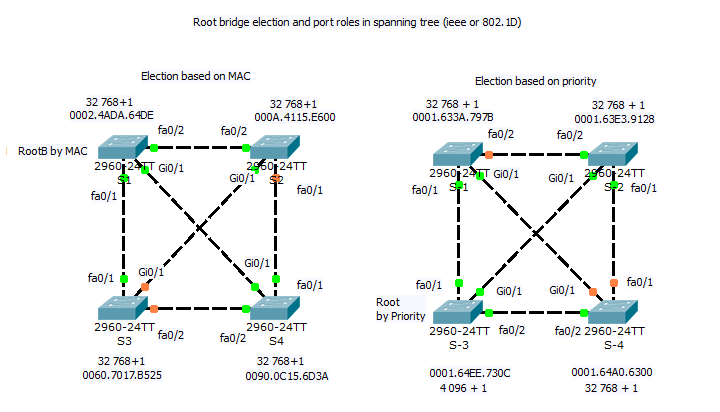
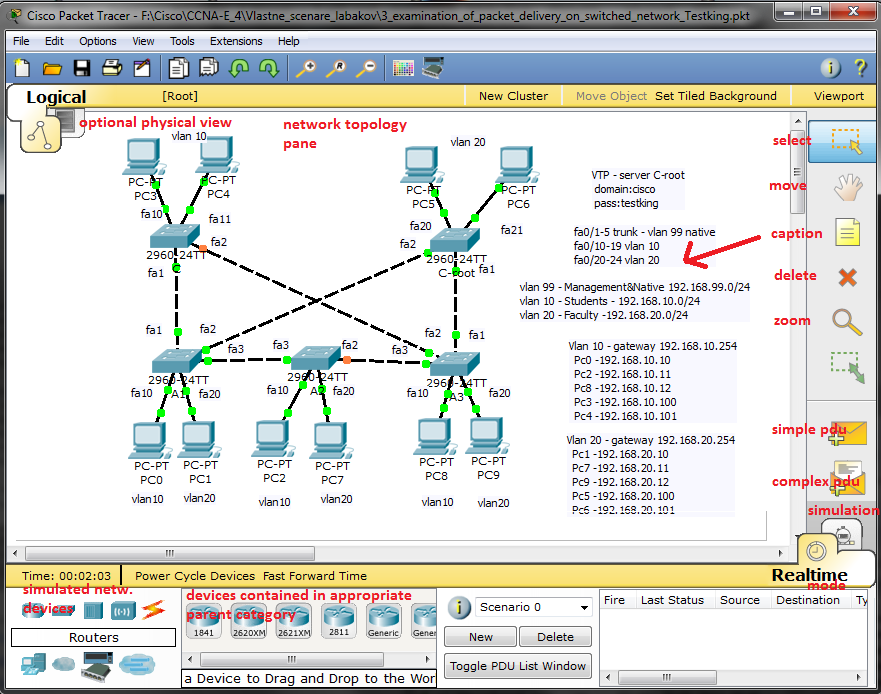
Our training scenario focused on port-security can be obtained from here (Packet tracer 5.2 or above you will need).
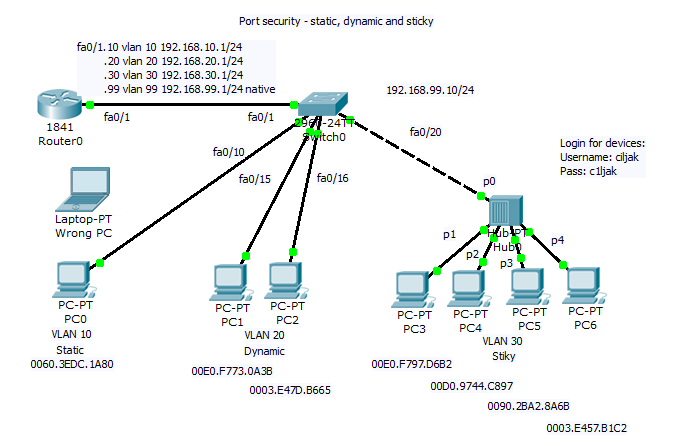
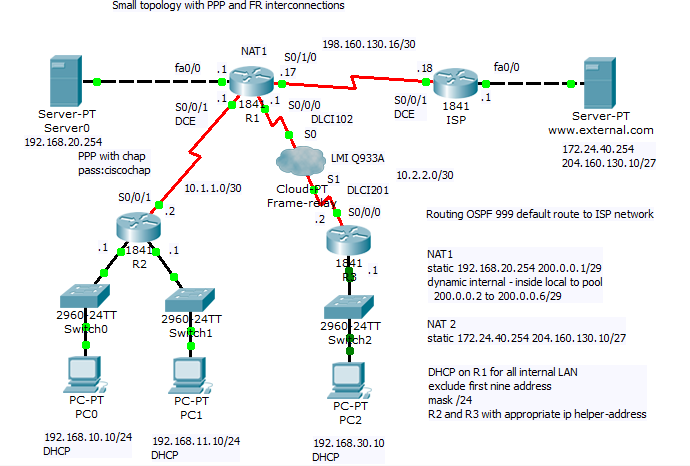
Network topology consist of router acting on stick and switch. Port security is configured sticky for 10 mac address for port 20 to 24 with commands:
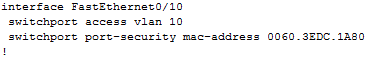
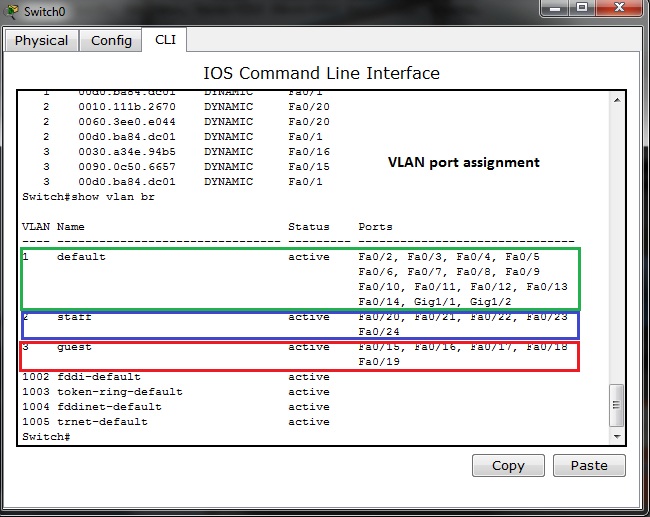
2) Enable dynamic learning for PC on ports fa0/15 and fa0/16.
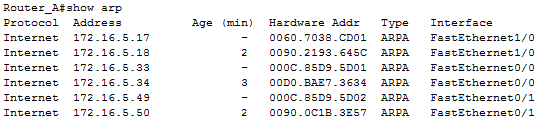
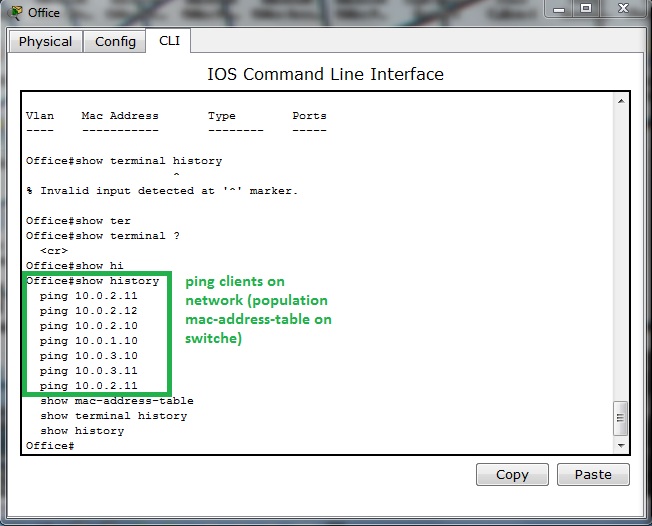
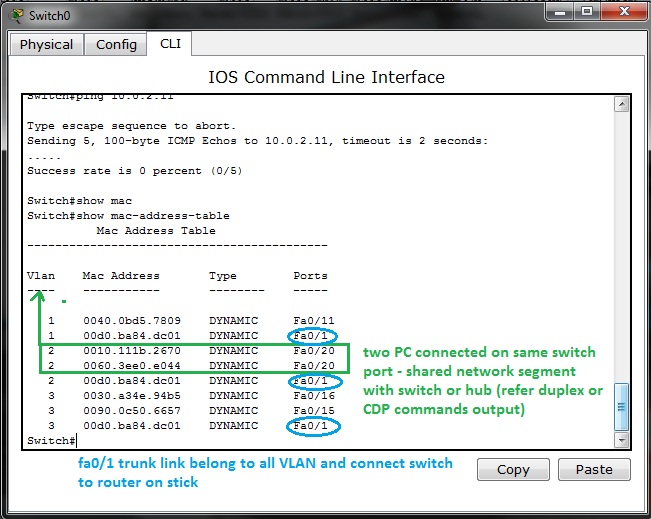
As example, output from show mac-address-table of switch
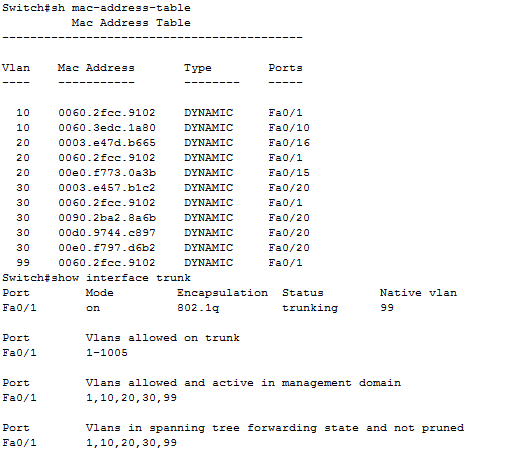
On port fa0/20 can be spot shared network segment (in our case it is hub interconnected segment).